Abstract: At least since the beginning of the most recent Russian invasion of Ukraine and the massive use of unmanned aerial vehicles, it has become imperative to elaborate potential countermeasures, that is, counter-unmanned aerial systems. Accordingly, based on past and ongoing conflicts – including the war in Ukraine – this paper analyses the impact of technological changes on warfare. Specifically, it takes a closer look at the types of unmanned aerial vehicles deployed on the modern battlefield and how critical infrastructure, soldiers and civilian populations could be protected in the face of these novel threats.
Problem statement: How can advancements in electronic and electrotechnical components contribute to the development of effective countermeasures against emerging asymmetric threats?
So what?: The diversity of technical disciplines such as AI, cybersecurity, electronic warfare, and necessary robustness requires close cooperation between government agencies, defence contractors, academic institutions, and military stakeholders to significantly accelerate the development and procurement process of counter-UAV technology.

Source: shutterstock.com/Shutterstock AI
Disruptive Technology
The barriers to entry for operating a UAV (Unmanned Aerial Vehicle) have decreased significantly over the years. Falling prices and comprehensive assistance systems offer even beginners a rapid learning curve to perform flight manoeuvres. As such, UAVs are no longer reserved exclusively for model-building experts. Major players in the drone market ensure that professionals, hobbyists, and technology enthusiasts have access to UAVs.[1] This simplified and uncontrolled access to UAVs is increasing disruption of the lower airspace in the civilian sector, albeit with a growing utility in military operations. The associated risks are significant, as UAVs can potentially penetrate sensitive areas. Typical incidents in the civilian sector may include intrusion or overflight of airports, industrial facilities, correctional institutions, barracks, military training grounds, and many other particularly protected buildings or areas. These incidents pose a challenge to air safety and raise significant legal and ethical questions that are becoming increasingly relevant in today’s society. Since the beginning of Russia’s invasion of Ukraine in 2022, UAVs have increasingly come into focus in modern warfare. A well-known quote from Lieutenant Colonel Thomas R. Stone (U.S. Army Field Artillery) illustrates this approach: “Never send an infantryman where you can send an artillery shell“.[2]
In this context, an artillery shell or projectile can metaphorically be a UAV. Historically, UAVs have been used in warfare for many years. The U.S. Air Force has been using Unmanned Aerial Systems (UAS), such as the RQ-1 Predator from General Atomics Aeronautical Systems, since 1997.[3] Today, small UAVs are being used in various conflicts, showing that they can not only carry out reconnaissance missions but also destroy infrastructure or even armoured military vehicles with minimal effort. Affordable, Commercial-Off-The-Shelf (COTS) hardware, which has seen no significant technological advancements in recent years, is now in direct competition with the most advanced military technology.
Effects on Warfare
Both reconnaissance and offensive UAV-based operations, such as airdropping bombs or missiles or kamikaze attacks, come with inherent risks, including detection by enemy forces, electronic countermeasures, or mission failure due to technical malfunctions. Therefore, it is important to understand the capabilities of UAVs and how they can be used in both offensive and defensive warfare. UAVs are either very fast and agile or fast and more stable, depending on payload requirements. The agility of a UAV is determined by its size, weight and construction.[4] They are divided into four categories — fixed-wing, single-rotor, multirotor and fixed-wing hybrid.[5], [6] Typical ranges for fixed-wing operations range from 500 km to over 1000 km.[7] Multirotors, which are more agile than fixed-wing UAS, can operate up to several kilometres (e.g., DJI specifies ranges between 13 km and 35 km).[8]
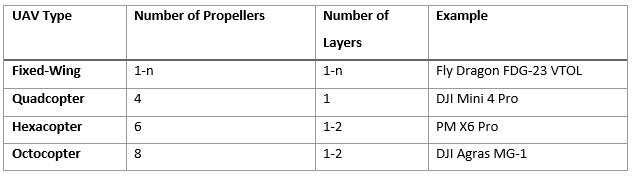
Example of different UAV types depending on the number of propellers and layers; Source: Author.
The “layers” mentioned in Column 3 of Table 1 refer to the arrangement of motors horizontally, without any height difference. If, for example, two motors are installed one above the other, this is referred to as two layers (as is the case with octocopters). The different UAV types come with specific advantages and disadvantages. The manoeuvrability of a multirotor is much better than that of fixed-wing aircraft. On the other hand, fixed-wing aircraft are much more efficient, resulting in improved flight duration and payload.
UAVs can also be used as loitering munitions via kamikaze attacks or dropping explosives on a target. In addition, the offensive use of UAVs to gather intelligence while psychologically harming the enemy through their mere presence should not be overlooked. In the civilian sector, UAVs declared offensive are mostly used for surveillance, spying on people or objects or smuggling goods.[9], [10]
![DIY FPV UAV with explosive.[11]](https://tdhj.org/wp-content/uploads/2025/05/Tebbe_2.jpg)
DIY FPV UAV with explosive.[11]
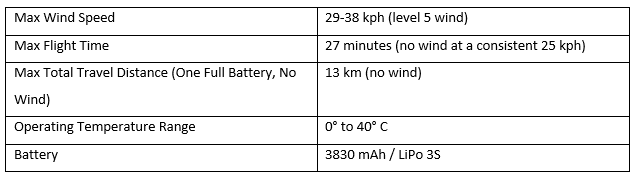
Overview of technical specifications from a general-purpose COTS-UAV, represented by DJI Mavic.
A GNSS is used to determine the position (longitude, latitude, and altitude) of targets. In principle, the receiving device (i.e., the UAV) must receive signals from at least four different satellites simultaneously to determine the three positional factors in Euclidean space along with the timing offset. Each GNSS satellite is equipped with a precise atomic clock, and the satellite transmits its local time when the signal was sent and its exact position in space (ephemeris data) at that time. As data is transmitted at the speed of light, the receiver can determine the distance to each satellite by calculating the time it took for the signal to travel.[13] However, threat techniques, such as jamming, can be used to manipulate the link between the UAV and the satellite system. Jamming means that the GNSS signal is interfered with by a signal in the same frequency band at a much higher power. Since 2022, the GPSJAM website has visualised GPS interference (i.e., jamming, spoofing, atmospheric conditions, etc.) based on aircraft reports on the accuracy of their navigation systems.[14]
![GPS Interferences in North, East and Central Europe in 2023 and 2024, respectively. Note: The border regions of Russia are clearly jammed in 2024.[15]](https://tdhj.org/wp-content/uploads/2025/05/Tebbe_4.png)
GPS Interferences in North, East and Central Europe in 2023 and 2024, respectively. Note: The border regions of Russia are clearly jammed in 2024.[15]
State-of-the-Art Drone Technology
The components of a UAV are mostly identical regardless of the UAV type. A basic UAV consists of a frame, motors, propellers, a battery, a flight control unit (FCU), a camera, and a remote control.

In recent years, UAVs have become increasingly sophisticated, with advancements in sensors and artificial intelligence (AI) leading to enhanced navigational precision in disturbed environments and areas with radio interference. It is important to note that flight controllers are designed to perform a consistent function: maintaining the flight path of a UAV by utilising onboard sensors, such as the inertial measurement unit, to control the individual motors through electronic speed controllers. Research projects, as well as the prevailing trend, are moving towards connecting additional high-performance computers to the flight controller for taking over computationally intensive algorithms (e.g., camera tracking, collision avoidance, simultaneous localisation and Mapping, and radio frequency (RF) sniffing) and controlling the FCU.[16], [17]
Another trend born out of necessity, which could be considered a technological step backwards, offers an enormous advantage on the battlefield, namely, the use of fibre optics as a transmission medium for controlling the UAV and transmitting video signals.[18], [19] The concept of utilising fibre-optic controlled UAVs, or, more specifically, wired UAVs, can be traced back to the principle of guiding missiles by sight via a wire, called Manual Command Line of Sight (MCLOS) systems.
![FPV UAV equipped with fibre optics.[20]](https://tdhj.org/wp-content/uploads/2025/05/Tebbe_6.jpg)
FPV UAV equipped with fibre optics.[20]
In general, UAV simulators are a great way to safely learn how to fly a UAV. They are cheap, easy to learn, and offer a realistic flight experience — even with the ability to modify the weather, time, and most importantly, the setup of the UAV (i.e., battery type, motors, propellers, frame, etc.). A vital consideration in the utilisation of a simulator pertains to not only the economic dimension, encompassing minimal hardware expenditure, but also the imperative of safeguarding against hardware degradation resulting from crashes.
![Comparison of some FPV-UAV simulators.[22]](https://tdhj.org/wp-content/uploads/2025/05/Tebbe_7.png)
Comparison of some FPV-UAV simulators.[22]

Counter-UAS
Defence against UAVs requires a comprehensive system capable of detecting targets over several kilometres to initiate early defence mechanisms like starting an interceptor UAS or using stationary systems. All mechanisms can be divided into soft kill mechanisms, like catching, jamming, and spoofing, or hard kill mechanisms like destroying or damaging targets to impair their flying ability. The great variety of UAV types presents significant challenges to defence systems, necessitating the integration of diverse sensors to facilitate seamless integration into an existing infrastructure. This integration is of paramount importance for the effective utilisation of these systems in both military and police environments. Most systems available on the market rely primarily on ground-based systems that use radars, cameras, and RF components. For instance, a machine gun mounted on a platform or an antenna with strong directional characteristics can be utilised. Another approach is using UAS to defend against smaller UAS (sUAS). Utilising a flying system confers numerous advantages, chief among them being the attainment of high flexibility and mobility. Moreover, especially for civil environments or where hard-kill solutions are prohibited, such a system facilitates the capture of a target using a net, which can then be transported away in a predefined manner. This aspect assumes particular significance when explosives are attached to the unauthorised system.
![Argus Interception Interceptor Drone with 3 Netguns.[23]](https://tdhj.org/wp-content/uploads/2025/05/Tebbe_9.jpg)
Argus Interception Interceptor Drone with 3 Netguns.[23]
UAS in the Ukraine-Russia War
The Shahed 136, built by an Iranian company called Iran Aircraft Manufacturing Industrial Company, is estimated to have an approximate range of 6-12,5 hours. This fixed-wing aircraft has already been deployed in Yemen and under the name Geran-2 in Ukraine. Equipped with an explosive warhead weighing up to 50 kg, this system is very difficult to detect using existing systems like Iron Dome or David’s Sling due to a low radar cross-section and its low speed of only 50 m/s to 67 m/s and a resulting smaller Doppler shift compared to classic guided missiles with a speed of Mach 3 or 1029 m/s.[24]
Initially, COTS UAS, such as the DJI Mavic 3, were employed as reconnaissance vehicles, but with minimal adjustments and the use of 3D-printed attachments, explosives such as hand grenades have also been deployed from the air. In addition to COTS UAS, the utilisation of self-built, so-called DIY UAVs is on the rise owing to their remarkably higher agility and speed. The open-source community of FCUs, coupled with the flexibility offered by the components, has led to a surge in their adoption. The COTS UAS predominantly converts control and video signals through 2.4 GHz or 5.8 GHz frequencies. However, depending on the country code and the UAS software, certain channels or entire frequency bands are automatically deactivated. While these digital systems incur significantly higher costs than their analogue alternatives, they offer the advantage of encrypted communication. The FPV UAS, colloquially referred to as racing drones, employ analogue video transmission with fibre optics to ensure interference-free and tamper-proof transmission. Consequently, within Ukraine, there has been a notable increase in the usage of homemade FPV UAS equipped with fibre optics.
Military Mindset
UAVs, as a growing asymmetric threat, must be addressed as a core component of basic training for soldiers. While advanced countermeasure techniques remain system-specific and, therefore, only part of the special training for specialised units, general awareness and response protocols should be embedded in the basic training of all soldiers. Given the broad spectrum of UAV applications, training curricula must account for both COTS-UAVs, such as those produced by DJI, and DIY-UAVs. The duration of the learning process depends on the specific and desired type of operation.
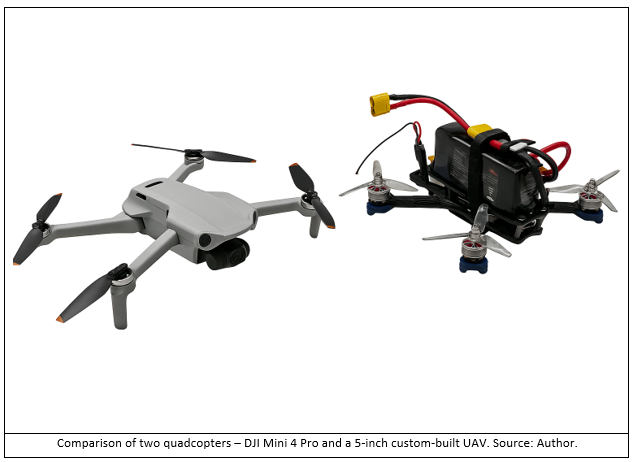
There are two approaches to the operation of a UAV. First, there is the option of conducting a training program in a simulator and attending flying lessons afterwards. Second, there is the option of attending only flying lessons. From the experience gained, it can be deduced that a COTS UAV equipped with auxiliary functions, such as collision avoidance, renders it possible to commence flight operations immediately without the prerequisite of prior experience.
Compared to COTS-UAVs, operating an FPV UAV needs slightly more training and experience, depending on the mission. The risk of a crash is elevated to a considerable degree in the former case due to the absence of software support, thus necessitating flight operations in a simulator. Military equipment and training can be very expensive for traditional weapons and vehicles like tanks or fighter jets. However, using a simulator with minimal hardware requirements to train soldiers in drone usage can save a lot of money and time. The running costs of a simulator are negligibly low, which makes it perfect for training purposes. The average cost of a UAV is around 500 USD, and the remote is between 50 and 200 USD. The military training inside simulators can practically be anywhere and anytime — there is no need for a big training area or lots of equipment.
The learning curve of a simulator is very steep. Even if there is no experience of flying an FPV-UAV, most simulators offer a tutorial to get started. Due to realistic physics and the ability to modify the controls, the user can learn how to fly a UAV quickly.[25] Personal experience shows that an FPV-UAV can be kept safely in the air after just a few hours (approx. 2-3 hours) of practice in the simulator. Agile, acrobatic flight manoeuvres in urban terrain, however, require significantly longer periods of practice, ranging up to an estimated simulator time of over 50 hours.
Another significant advantage of a simulator is the immersive virtual experience of being on the battlefield, which it recreates without any associated risks. The integration of advanced graphics, a diverse array of maps, and a range of tasks, including races, freestyle, airdrops, and kamikaze, enhances this immersive experience.
![A still of footage from an FPV Kamikaze Drone Simulator.[26]](https://tdhj.org/wp-content/plugins/wp-fastest-cache-premium/pro/images/blank.gif)
A still of footage from an FPV Kamikaze Drone Simulator.[26]
Sensitising
With dimensions ranging from that of a human fist up to a wingspan spanning several meters, UAVs are characterised by their speed and elusiveness, rendering reconnaissance without sensor-supported systems virtually impossible. It is also necessary to emphasise the importance of safeguarding critical infrastructures, including command posts, positions, and radio relay stations. The demand for robust safeguarding becomes even more urgent in light of the evolving threat landscape–particularly the increasing incidence of UAV intrusions, which necessitate timely and effective response strategies. The importance of such protection extends beyond the battlefield, encompassing military training areas, critical infrastructures, and industrial facilities in peacetime. Ensuring the security of these entities is vital to protect against potential interference, espionage, and disruption.
Contrary to being self-evident, this observation highlights a critical and often underestimated challenge in contemporary airspace monitoring. The combination of reduced visual signature, high manoeuvrability, and low-altitude operation significantly impairs human detection capabilities, even under optimal visual conditions. This underscores the necessity for advanced detection systems beyond human perception.
Changes in Warfare
Military deployment of UAVs has changed the way wars are fought. The Russia-Ukraine War has demonstrated that the threat posed by UAVs is ubiquitous. Specifically, deploying the most economical UAVs, estimated to cost between 300–400 USD, in conjunction with the adept installation of a mount or an airdrop mechanism, is sufficient to destroy several million USD worth of armour.[27]
![FPV UAV Destroying T-90 Tank.[28]](https://tdhj.org/wp-content/uploads/2025/05/Tebbe_12.png)
FPV UAV Destroying T-90 Tank.[28]
In contemporary military operations, the prevalence of one-to-one attacks, and occasionally, one-to-a-few individual targets, is common. This phenomenon can be attributed, in part, to the constrained carrying capacity and flight duration of a solitary UAS, which comprises a UAV along with its supporting equipment, such as a ground control station and communication links. It is postulated that the future of UAS-supported warfare will be characterised by a symbiotic integration of drones operating in air, ground, and water domains. The capabilities of individual UAS have been demonstrated in a range of conflicts. The consequences of deploying multiple UAVs as a swarm, utilising AI-supported analysis to identify vulnerabilities and allocate targets, are of particular concern. The prospect of a swarm of autonomously operating ‘search heads’ poses a significant threat.
![UAV Swarm starting from a ship.[30]](https://tdhj.org/wp-content/uploads/2025/05/Tebbe_13.jpg)
UAV Swarm starting from a ship.[30]
Conclusion and Outlook
In modern conflicts, both sides – the attacker and defender – must cope with rapidly evolving warfare owing to UAVs being deployed in different use cases. The chance of success in using a UAV for offensive purposes is significantly higher than that of intercepting or defending against a single UAV, not to mention swarms of UAVs. Developing and researching defence mechanisms is a more difficult and costly process than adapting existing systems and exploiting long-established sensor and actuator technology, in conjunction with the substantial wealth of information available on the internet.
The contemporary generation of drones is derived from the sports sector of racing drones. These drones are neither robust nor designed for adverse environments; they are engineered to be extremely light and fast. However, should the military make significant investments in swarm intelligence to develop robust, military UAS, then the prospect of a completely autonomous UAS swarm, integrated into a command-and-control system, becomes a realistic possibility. Such a swarm could be deployed as part of a networked battlefield on land, at sea or in space, with the capability of detecting and destroying tactical targets.
Individual components are effectively standardised and can be assembled into a functioning UAV and operated without a great deal of prior knowledge. However, the main challenge in the future will be creating supply chains for components so that there is little dependence on individual manufacturers. Additionally, the focus has now shifted from optimising hardware in terms of weight, speed, endurance, and agility to developing software increasingly dependent on AI to reliably facilitate automated or autonomous missions in the most adverse environments. On the C-UAS side, these advances need to be implemented in a system that uses multi-sensor and (multi-) actuator technology to prevent imminent attack vectors.
This is why, for example, the Chair of Electrical Measurement Engineering at the University of the Federal Armed Forces Hamburg has focused on the development of an air-based multi-sensor system for drone defence as a basic concept to cope with a variety of different drone types and threats. It can be easily deployed for military and civil applications using private 5G mobile radio as a robust swarm communication system. Furthermore, AI-based detection and classification, primarily using cameras instead of RADAR sensors, make the system invisible to the electromagnetic reconnaissance of hostile observers. The system will also be enhanced to operate in GNSS-denied environments.
Nevertheless, several limitations of the current system architecture must be acknowledged. While advantageous in terms of electromagnetic signature reduction, the exclusive reliance on electro-optical sensors for detection and classification inherently constrains operational effectiveness under suboptimal environmental conditions, such as low illumination, adverse weather, or high-contrast background scenarios. Furthermore, the operational resilience and security of private 5 G-based swarm communication networks in electronically contested or degraded signal environments have not yet been comprehensively validated. In light of these constraints, future research should prioritise the multimodal fusion of heterogeneous sensor data, incorporating passive RF sensing, thermal imaging, and acoustic signatures to enhance detection robustness across diverse environmental conditions. Additionally, systematic evaluation of the GT communication layer under simulated electronic warfare scenarios is essential to assess its viability in contested domains. Further efforts should also be directed toward developing advanced onboard autonomy for distributed decision-making and systematic system performance assessment in GNSS-denied and spoofed environments, to ensure operational integrity and mission resilience.
Captain Kevin Tebbe, M.Sc., Autonomous C-UAS UAS Swarms, 5G Cellular Communication; M.Sc. Robert Pommeranz; Autonomous C-UAS UAS Swarms, Computer Vision, Object Tracking; Major (Reserve) Dr.-Ing. Ralf Heynicke; Head of Laboratory; C-UAS UAS, Industrial Communication; Univ.-Prof. Dr.-Ing. Gerd Scholl, Head of Chair for Electrical Measurement Engineering.
The views contained in this article are the authors’ alone and do not represent the official opinion of the German Armed Forces.
[1] “Drohnen – Deutschland | Statista Marktprognose,” Statista, accessed December 13, 2024, https://de.statista.com/outlook/cmo/consumer-electronics/drohnen/deutschland.
[2] “Never Send an Infantryman Where You Can Send an Artillery Shell,” accessed December 13, 2024, https://apps.dtic.mil/sti/citations/ADA089419.
[3] “General Atomics Aeronautical Systems RQ-1 Predator,” National Museum of the United States Air ForceTM, accessed December 13, 2024, https://www.nationalmuseum.af.mil/Visit/Museum-Exhibits/Fact-Sheets/Display/Article/196333/general-atomics-aeronautical-systems-rq-1-predator/https%3A%2F%2Fwww.nationalmuseum.af.mil%2FVisit%2FMuseum-Exhibits%2FFact-Sheets%2FDisplay%2FArticle%2F196333%2Fgeneral-atomics-aeronautical-systems-rq-1-predator%2F.
[4] “Power and Weight Considerations in Small, Agile, Quadrotors | Request PDF,” ResearchGate, October 22, 2024, https://doi.org/10.1117/12.2051112.
[5] “Drone Types: Multi-Rotor, Fixed-Wing, Single Rotor, Hybrid VTOL,” November 08, 2016, https://www.auav.com.au/articles/drone-types/.
[6] Wilfried Yves Hamilton Adoni et al., “Investigation of Autonomous Multi-UAV Systems for Target Detection in Distributed Environment: Current Developments and Open Challenges,” Drones 7, no. 4 (April 2023): 263, https://doi.org/10.3390/drones7040263.
[7] “Skyeye Long Range Fixed Wing UAV Drones SM200G,” Skyeye UAV, accessed April 22, 2025, https://www.skyeyeuav.com/products/skyeye-long-range-fixed-wing-uav-drones-sm200g.
[8] “DJI Matrice 4 Serie – Technische Daten,” DJI, accessed March 31, 2025, https://enterprise.dji.com/de/matrice-4-series/photo.
[9] Riham Altawy and Amr M. Youssef, “Security, Privacy, and Safety Aspects of Civilian Drones: A Survey,” ACM Trans. Cyber-Phys. Syst. 1, no. 2 (November 09, 2016): 7:1-7:25, https://doi.org/10.1145/3001836.
[10] “Schwerer Verlust für Russland: T-90-Panzer zerstört – Video zeigt Angriff,” October 27, 2023, https://www.fr.de/politik/kamikaze-drohne-ukraine-krieg-russland-verluste-panzer-t90-zerstoert-waffen-angriff-zr-92638194.html.
[11] “Paratroopers of the 79th Air Assault Brigade Received FPV Drones and Warheads from Volunteers,” Militarnyi (blog), accessed February 24, 2025, https://mil.in.ua/en/news/paratroopers-of-the-79th-air-assault-brigade-received-fpv-drones-and-warheads-from-volunteers/.
[12] “Mavic Pro – Produktinformationen – DJI,” DJI Official, accessed March 03, 2025, https://www.dji.com/de/mavic/info.
[13] “GPS-Compendium_Book_(GPS-X-02007).Pdf,” accessed March 3, 2025, https://content.u-blox.com/sites/default/files/products/documents/GPS-Compendium_Book_%28GPS-X-02007%29.pdf.
[14] “GPSJAM GPS/GNSS Interference Map,” accessed March 31, 2025, https://gpsjam.obliscence.com/.
[15] “GPSJAM GPS/GNSS Interference Map.”
[16] Nils Tijtgat et al., “Embedded Real-Time Object Detection for a UAV Warning System,” in 2017 IEEE International Conference on Computer Vision Workshops (ICCVW) (2017 IEEE International Conference on Computer Vision Workshop (ICCVW), Venice: IEEE, 2017), 2110–18, https://doi.org/10.1109/ICCVW.2017.247.
[17] Michael Mugnai et al., “An Efficient Framework for Autonomous UAV Missions in Partially-Unknown GNSS-Denied Environments,” Drones 7, no. 7 (July 2023): 471, https://doi.org/10.3390/drones7070471.
[18] David Hambling, “Russian Fiber Optic Drone Beats Any Jammer (UPDATE: Ukraine Version),” Forbes, accessed February 27, 2025, https://www.forbes.com/sites/davidhambling/2024/03/08/russian-fiber-optic-drone-can-beat-any-jammer/.
[19] “The Ministry of Defence showcased FPV | MoD News,” January 02, 2025, https://mod.gov.ua/en/news/the-ministry-of-defence-showcased-fpv-drones-controlled-using-fiber-optics-to-the-armed-forces-of-ukraine.
[20] “The Ministry of Defence showcased FPV | MoD News.”
[21] “UAV Optical Fiber Communication, Optical Fiber Communication FPV,” Skywalker technology, accessed February 27, 2025, https://skywalkerfpv.com/.
[22] “Comparing Charts for 6 Apps,” SteamDB, accessed February 25, 2025, https://steamdb.info/charts/?compare=410340,641780,1278060,1682970,1881200,2707940.
[23] “Die innovative Abfangdrohne von Argus Interception, accessed February 25, 2025,
https://argus-interception.com/de/”
[24] “Ukrainian AN-196 Liutyi Drone, Dubbed ‘Ukrainian Shahed,’ Receives Major Upgrade,” UNITED24 Media, November 25, 2024, https://united24media.com/latest-news/ukrainian-an-196-liutyi-drone-dubbed-ukrainian-shahed-receives-major-upgrade-3996.
[25] Dante Tezza, Denis Laesker, and Marvin Andujar, “The Learning Experience of Becoming a FPV Drone Pilot,” in Companion of the 2021 ACM/IEEE International Conference on Human-Robot Interaction, HRI ’21 Companion (New York, NY, USA: Association for Computing Machinery, 2021), 239–41, https://doi.org/10.1145/3434074.3447167.
[26] “Sparen Sie 50% bei FPV Kamikaze Drone auf Steam,” accessed March 05, 2025, https://store.steampowered.com/app/2707940/FPV_Kamikaze_Drone/.
[27] “Schwerer Verlust für Russland.”
[28] Defence of Ukraine [@DefenceU], “The Occupiers Are Quite Proud of Their T-90 Tanks. Watch How One of Them Is Destroyed by a Ukrainian FPV Drone. 📹: Asgard Group Https://T.Co/A9YeK9unPd,” Tweet, Twitter, October 24, 2023, https://x.com/DefenceU/status/1716899863525552446.
[29] Typoheads GmbH, “Von Drohnen und Panzern: Zehn Fragen an Oberst Markus Reisner,” May 14, 2024, https://www.bundesheer.at/aktuelles/detail/von-drohnen-und-panzern-zehn-fragen-an-oberst-markus-reisner.
[30] The Future of Warfare | Palantir, 2024, https://www.youtube.com/watch?v=UiiqiaUBAL8.




